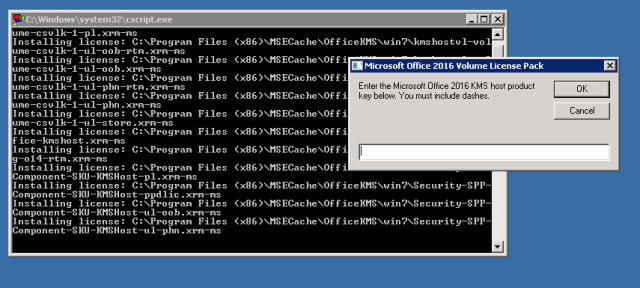
I needed a list of the built-in security roles in System Center Configuration Manager, but couldn’t find a list in the Microsoft documentation. The roles and descriptions can be found in the Configuration Manager console under Administration > Security > Security Roles.
This list is a compilation of the roles listed in the console as of Current Branch 1806.
Application Administrator
Grants permissions to perform both the Application Deployment Manager role and the Application Author role. Administrative users who are associated with this role can also manage queries, view site settings, manage collections, edit settings for user device affinity, and manage App-V virtual environments
Application Author
Grants permissions to create, modify, and retire applications. Administrative users who are associated with this role can also manage applications, packages, and App-V virtual environments.
Application Deployment Manager
Grants permissions to deploy applications. Administrative users who are associated with this role can view a list of applications, and they can manage deployments for applications, alerts, templates and packages, and programs. Administrative users who are associated with this role can also view collections and their members, status messages, queries, conditional delivery rules, and App-V virtual environments.
Asset Manager
Grants permissions to manage the Asset Intelligence Synchronization Point, Asset Intelligence reporting classes, software inventory, hardware inventory, and metering rules.
Company Resource Access Manager
Grants permissions to create, manage and deploy company resource access profiles such as Wi-Fi, VPN, Exchange ActiveSync email, and certificate profiles to users and devices.
Compliance Settings Manager
Grants permissions to define and monitor Compliance Settings. Administrative users associated with this role can create, modify, and delete configuration items and baselines. They can also deploy configuration baselines to collections, and initiate compliance evaluation, and initiate remediation for non-compliant computers.
Endpoint Protection Manager
Grants permissions to define and monitor security policies. Administrative Users who are associated with this role can create, modify and delete Endpoint Protection policies. They can also deploy Endpoint Protection policies to collections, create and modify Alerts and monitor Endpoint Protection status.
Full Administrator
Grants all permissions in Configuration Manager. The administrative user who first creates a new Configuration Manager installation is associated with this security role, all scopes, and all collections.
Infrastructure Administrator
Grants permissions to create, delete, and modify the Configuration Manager server infrastructure and to perform migration tasks.
Operating System Deployment Manager
Grants permissions to create operating system images and deploy them to computers. Administrative users who are associated with this role can manage operating system upgrade packages and images, task sequences, drivers, boot images, and state migration settings.
Operations Administrator
Grants permissions for all actions in Configuration Manager except for the permissions that are required to manage security, which includes managing administrative users, security roles, and security scopes.
Read-only Analyst
Grants permissions to view all Configuration Manager objects.
Remote Tools Operator
Grants permissions to run and audit the remote administration tools that help users resolve computer issues. Administrative users that are associated with this role can run Remote Control, Remote Assistance and Remote Desktop from the Configuration Manager console. In addition, they can run the Out of Band Management console and AMT power control options.
Security Administrator
Grants permissions to add and remove administrative users and to associate administrative users with security roles, collections, and security scopes. Administrative users who are associated with this role can also create, modify, and delete security roles and their assigned security scopes and collections.
Software Update Manager
Grants permissions to define and deploy software updates. Administrative users who are associated with this role can manage software update groups, deployments, and deployment templates.